In an age defined by digital interconnectedness, our data security faces an unprecedented challenge: the advent of fault-tolerant quantum computers. These powerful machines, while still developing, possess the theoretical capability to break the very cryptographic algorithms that secure our online lives today – from banking to government communications. This looming threat has rapidly elevated Post-Quantum Cryptography (PQC) to a global cybersecurity imperative. As of mid-2025, the race is on to deploy new cryptographic methods that can withstand future quantum attacks, ensuring the long-term integrity and confidentiality of our digital world.
What is Post-Quantum Cryptography (PQC)?
Post-Quantum Cryptography (PQC), also known as quantum-resistant cryptography, refers to a set of cryptographic algorithms that are designed to be secure against attacks by both classical (traditional) and future quantum computers. The goal of PQC is to replace the current generation of widely used public-key cryptographic algorithms, which are vulnerable to quantum computing advancements.
Unlike current encryption methods that rely on mathematical problems difficult for classical computers to solve (like factoring large numbers or discrete logarithms), PQC algorithms are based on different “hard” mathematical problems that are believed to remain intractable even for powerful quantum machines. This ensures that our digital locks remain unbroken even when quantum computers become a widespread reality.
The Quantum Threat: Why PQC is Critical Now
The urgency around Post-Quantum Cryptography stems directly from the theoretical capabilities of large-scale quantum computers. Two key quantum algorithms pose the most significant threat to current cryptography :
- Shor’s Algorithm: Discovered by Peter Shor in 1994, this algorithm can efficiently solve the integer factorization problem and the discrete logarithm problem. These two problems form the mathematical backbone of widely used public-key encryption schemes such as RSA and Elliptic Curve Cryptography (ECC), which are foundational to TLS/SSL (securing web traffic), digital signatures, and many other security protocols. A sufficiently powerful quantum computer running Shor’s algorithm could decrypt virtually all currently encrypted public-key communications, including past “captured” encrypted data. This is known as the “Harvest Now, Decrypt Later” threat.
- Grover’s Algorithm: While not breaking symmetric-key cryptography (like AES) entirely, Grover’s algorithm can significantly speed up brute-force attacks. It can effectively halve the security strength of a symmetric key. For example, a 128-bit AES key would effectively have only 64 bits of security against a quantum attack using Grover’s algorithm, making it vulnerable to brute-force attacks by quantum computers. This means current key lengths would need to be doubled for equivalent security.
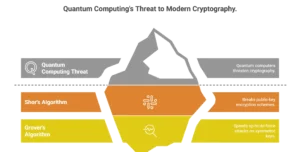
The critical takeaway is that once large-scale quantum computers become available (a timeline often debated but estimated between 10-20 years from now by experts), they will render a vast portion of our existing digital security infrastructure obsolete. Given the long implementation cycles for cryptographic updates across global systems, the transition to PQC needs to begin now.
How PQC Differs from Current Cryptography
The fundamental difference between current (classical) cryptography and Post-Quantum Cryptography lies in the mathematical problems they leverage to ensure security.
The shift to PQC involves abandoning mathematically “easy” problems for quantum computers in favor of new, quantum-resistant mathematical structures.
Key Families of Post-Quantum Algorithms
Researchers worldwide are developing and evaluating various families of algorithms for Post-Quantum Cryptography. Each family is based on different complex mathematical problems, offering diverse security properties and performance characteristics.
The selection of diverse families aims to ensure that if one mathematical problem turns out to be vulnerable to future quantum attacks, other, different approaches will remain secure.
The NIST Standardization Process and Beyond
The National Institute of Standards and Technology (NIST) has been at the forefront of the global effort to standardize Post-Quantum Cryptography. Their multi-year competition, launched in 2016, aimed to solicit, evaluate, and standardize quantum-resistant public-key cryptographic algorithms.
Key Milestones and Selections (as of mid-2025):
- Third Round (July 2022): NIST announced the first set of algorithms to be standardized.
- Primary Algorithms:
- CRYSTALS-Kyber: Selected as the primary algorithm for Key-Encapsulation Mechanisms (KEMs), used for establishing secret keys over insecure channels. It is lattice-based.
- CRYSTALS-Dilithium: Selected as the primary algorithm for Digital Signatures, used for authenticating digital messages and documents. It is also lattice-based.
- Alternative Algorithms:
- Falcon: A digital signature algorithm (lattice-based), chosen as an alternative to Dilithium.
- SPHINCS+: A digital signature algorithm (hash-based), chosen as a stateless alternative, offering very high security assurance, though with larger signatures.
- Primary Algorithms:
- Fourth Round (Ongoing): NIST continued to evaluate a few remaining algorithms for additional standards, particularly for KEMs with different characteristics (e.g., smaller keys or better performance for specific use cases). Classic McEliece (code-based) was selected as an alternative KEM in early 2024, providing a diverse underlying mathematical problem.
The standardization process is crucial because it provides the industry with agreed-upon algorithms that have undergone rigorous public scrutiny and peer review, paving the way for widespread adoption. Organizations should stay updated on NIST’s progress, as these standards will dictate future cryptographic implementations. More details on the NIST PQC standardization can be found on their official NIST Post-Quantum Cryptography Standardization website.
The Challenge of Quantum-Safe Migration
Migrating global digital infrastructure to Post-Quantum Cryptography is a monumental undertaking, often compared to the Y2K bug or the transition from IPv4 to IPv6, but potentially more complex. It’s not a simple software update; it involves every system that relies on public-key cryptography.
Key Challenges:
- Scale and Complexity: Identifying and updating every piece of hardware, software, and protocol that uses vulnerable cryptography (from embedded devices and IoT to cloud services and legacy systems) is a massive inventory and deployment challenge.
- Cost: The financial investment required for this global upgrade will be substantial, encompassing research, development, testing, and deployment across countless systems.
- “Crypto-Agility”: Organizations need to develop the capability to rapidly swap out cryptographic algorithms in their systems. This means designing systems that are “crypto-agile,” allowing for flexible updates rather than hardcoding algorithms. This will be essential not just for the quantum transition but for future cryptographic updates.
- Performance Trade-offs: Some PQC algorithms might have larger key sizes, slower encryption/decryption speeds, or larger signature sizes compared to their classical counterparts, potentially impacting performance in resource-constrained environments.
- Interoperability: Ensuring that new PQC implementations can communicate seamlessly with existing systems during a phased migration, often through “hybrid mode” implementations (running both classical and PQC algorithms simultaneously).
- Skills Gap: A shortage of cryptographic experts and engineers who understand PQC and can implement it correctly.
- Timeline: The “Harvest Now, Decrypt Later” threat means that even data encrypted today could be decrypted in the future. This necessitates protecting long-lived sensitive data with PQC now, before quantum computers fully mature.
Organizations are beginning to assess their cryptographic dependencies and develop migration roadmaps. This typically involves a multi-phase approach: discovery and inventory, risk assessment, pilot deployments, and eventual broad implementation. The emphasis is on proactive preparation rather than reactive scrambling when the quantum threat becomes imminent.
The Future of Secure Communication
The journey into the age of Post-Quantum Cryptography is well underway. While the full realization of large-scale, fault-tolerant quantum computers might still be a decade or more away, the work on PQC is a testament to the foresight and collaborative efforts of cryptographers, computer scientists, and governments worldwide. This proactive stance ensures that the fundamental pillars of our digital society—confidentiality, integrity, and authenticity—remain robust in the face of unprecedented computational power.
The transition will be complex, costly, and demand significant coordination. However, success in this endeavor will usher in a new era of secure communication, safeguarding our digital interactions, sensitive data, and critical infrastructure against a formidable future threat. The dawn of quantum-safe cryptography is not just about defending against a theoretical possibility; it’s about building a more resilient and trustworthy digital future for everyone.
Want to learn more about the cutting edge of cybersecurity and how emerging technologies are shaping our digital future? Explore our in-depth articles at jurnalin.