n the fast-paced world of modern software development, where speed and agility are paramount, security can no longer be an afterthought. This reality has given rise to the crucial practice of DevSecOps Maturity (Shift Left Security), a cultural and technological evolution that embeds security into every stage of the software development lifecycle, rather than treating it as a final-stage gate. As of mid-2025, organizations are increasingly recognizing that a mature DevSecOps approach is not just a best practice but a strategic imperative to build more resilient, compliant, and trustworthy software in an era of continuous delivery and escalating cyber threats.
Understanding DevSecOps and “Shift Left Security”
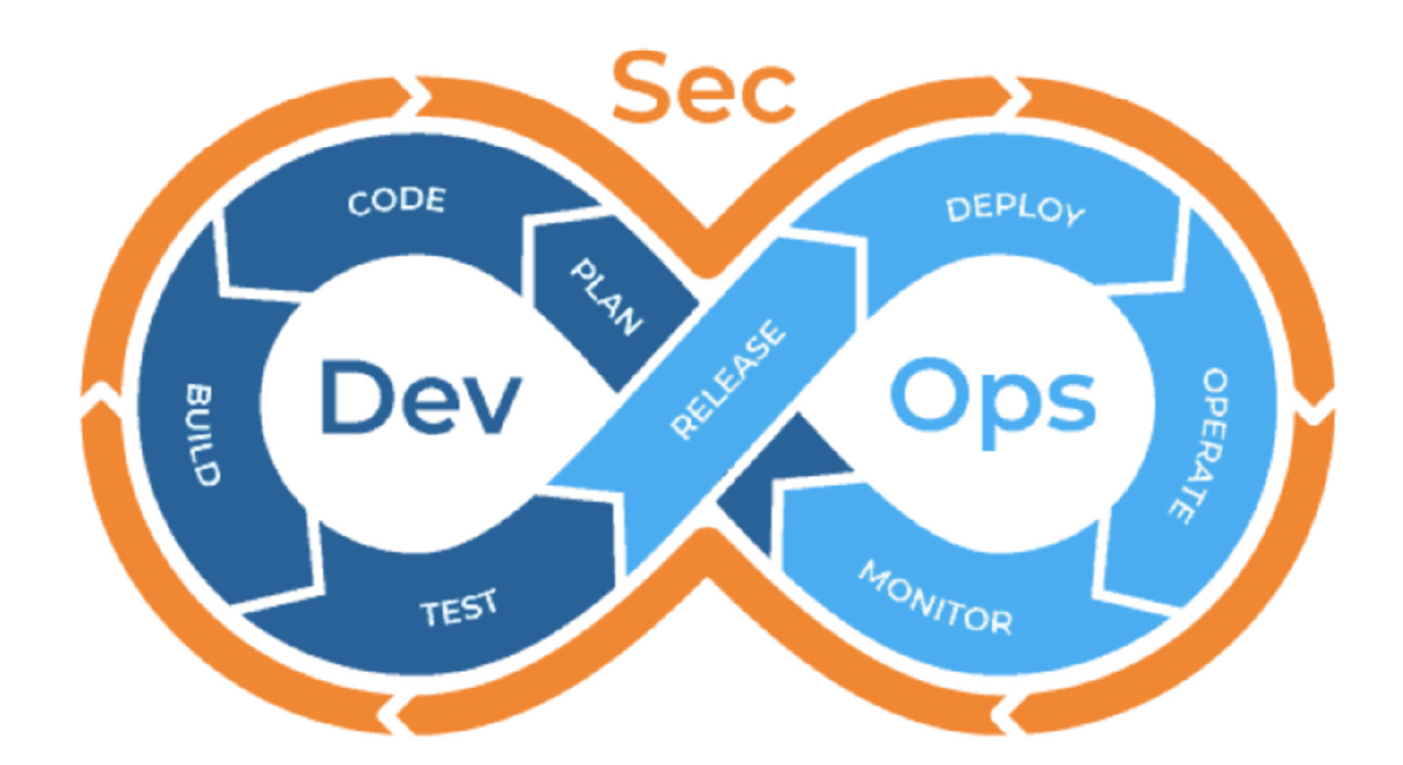
DevSecOps is the integration of security into the DevOps workflow. It’s a collaborative approach that automates security processes, promotes a security-first culture, and breaks down the traditional silos between development, security, and operations teams. Its core philosophy is to make security a shared responsibility.
The fundamental principle of DevSecOps is “Shift Left Security.” This concept advocates for moving security testing and analysis to the earliest possible stages of development—as far “left” as possible on the timeline. Instead of a security team only testing the final product just before deployment, Shift Left Security encourages developers to integrate security from the initial code commit and throughout the CI/CD (Continuous Integration/Continuous Deployment) pipeline.
Here’s how Shift Left Security contrasts with a traditional, siloed approach:
The objective of Shift Left Security is simple yet powerful: make it easier, faster, and cheaper to build secure software by catching and remediating vulnerabilities early.
The DevSecOps Maturity Model: From Ad-Hoc to Optimized
Achieving a high level of DevSecOps Maturity (Shift Left Security) is a journey, not a single event. Organizations can be classified into different maturity stages, each with its own characteristics, tools, and practices. Understanding this model is key to charting a path for improvement.
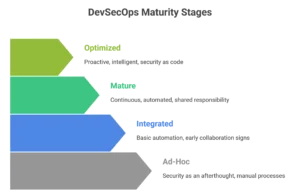
- Level 1: Ad-Hoc/Nascent
- Description: Security is an afterthought, often a manual and reactive process performed late in the development cycle. There is little to no automation or collaboration between teams.
- Practices: Manual penetration testing, vulnerability scanning only on production systems. Security is seen as a bottleneck.
- Mindset: “Security is not my job.”
- Level 2: Integrated/Basic
- Description: The organization has recognized the importance of security and is starting to integrate some automated tools into the CI/CD pipeline. There are early signs of collaboration.
- Practices: Automated Static Application Security Testing (SAST) and Software Composition Analysis (SCA) tools are introduced into the build process. Security is seen as a check-the-box requirement.
- Mindset: “Let’s use some tools to do security.”
- Level 3: Mature/Continuous
- Description: Security is a continuous, automated process that is fully integrated into the CI/CD pipeline. Teams are collaborative, and security is an accepted part of the daily workflow.
- Practices: SAST, DAST (Dynamic Application Security Testing), and SCA are run automatically and continuously. Security policies are codified and enforced in the pipeline. Continuous monitoring and feedback loops are in place.
- Mindset: “Security is a shared responsibility, and we own it.”
- Level 4: Optimized/Proactive
- Description: This is the highest level of DevSecOps Maturity. Security is not just automated but intelligent, predictive, and proactive. The organization has a security-as-code mindset.
- Practices: Predictive threat modeling, AI-powered security analytics, automated policy generation, chaos engineering for security, and a focus on building security into the architectural design phase. Security is seen as a competitive advantage.
- Mindset: “Security is a core part of our product’s value proposition.”
Most organizations today are somewhere between Level 2 and Level 3, actively working to mature their practices and tools to achieve greater efficiency and security.
Key Practices for Achieving DevSecOps Maturity
Building a mature DevSecOps culture requires a combination of people, processes, and technology. Here are the key practices to focus on :
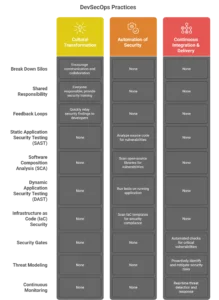
- Cultural Transformation (People):
- Break Down Silos: Encourage communication and collaboration between development, security, and operations teams. Security professionals should be embedded within development teams.
- Shared Responsibility: Foster a mindset where everyone is responsible for security. Provide security training and awareness programs for all developers.
- Feedback Loops: Ensure that security findings are fed back to developers quickly and clearly, so they can learn from mistakes and improve.
- Automation of Security (Technology):
- Static Application Security Testing (SAST): Integrate tools that analyze source code for vulnerabilities without running the application. This is a key “shift-left” practice.
- Software Composition Analysis (SCA): Automate the scanning of open-source and third-party libraries for known vulnerabilities (CVEs). This is critical, as open-source components are a major source of risk. For more on the importance of SCA, a detailed report from Synopsys on the State of Open Source Security provides valuable data.
- Dynamic Application Security Testing (DAST): Run automated tests on a running application to find vulnerabilities, simulating real-world attacks. This complements SAST.
- Infrastructure as Code (IaC) Security: Use tools to scan IaC templates (e.g., Terraform, Ansible) to ensure they comply with security policies before infrastructure is provisioned.
- Continuous Integration & Delivery (Process):
- Security Gates: Implement automated security gates in the CI/CD pipeline that can automatically fail a build if it contains critical vulnerabilities.
- Threat Modeling: Incorporate threat modeling into the design and planning phases of development to proactively identify and mitigate security risks.
- Continuous Monitoring: Use security tools that provide continuous monitoring of production environments to detect and respond to threats in real time. This “shift-left” also includes “shifting right” for ongoing vigilance. For a deeper understanding of CI/CD integration, the National Institute of Standards and Technology (NIST) has publications on secure software development, which are highly authoritative.
Benefits of a Mature DevSecOps Approach
A high level of DevSecOps Maturity (Shift Left Security) delivers significant benefits that improve both security posture and business outcomes.
- Faster Delivery of Secure Software: By finding and fixing vulnerabilities early, teams can avoid costly delays and last-minute security bottlenecks, enabling them to release software faster without compromising on security.
- Reduced Cost and Effort: The cost of fixing a vulnerability in the early stages of development is a fraction of the cost of fixing it in production. Shift Left Security saves time, money, and resources.
- Enhanced Security Posture: A mature DevSecOps program creates a proactive, preventative security posture rather than a reactive one. This significantly reduces the attack surface and minimizes the risk of data breaches.
- Improved Collaboration and Innovation: When security becomes a shared responsibility, it fosters a culture of collaboration and trust. Developers can innovate more freely, knowing that security is an integrated part of their workflow.
- Compliance and Governance: A mature DevSecOps pipeline automates the enforcement of security policies and provides a transparent audit trail of security checks, making it easier to meet regulatory and compliance requirements.
- Greater Business Resilience: By continuously monitoring and securing the entire software lifecycle, organizations build more resilient systems that can withstand and recover from cyber-attacks more effectively.
Overcoming Challenges to DevSecOps Implementation
While the benefits are clear, implementing a mature DevSecOps program is not without its challenges.
- Cultural Resistance: Developers may feel that security tasks are a burden that slows them down. Security teams may be resistant to relinquishing their traditional “gatekeeper” role. Overcoming this requires strong leadership, education, and buy-in from all stakeholders.
- Tooling and Integration: The landscape of DevSecOps tools is vast and can be complex to integrate. Choosing the right tools and ensuring they work seamlessly with existing CI/CD pipelines can be a significant technical challenge.
- Skill Gap: Many developers lack formal security training, and security professionals may lack an understanding of modern DevOps practices. Bridging this skill gap requires targeted training and upskilling programs. A good starting point for professional development is to explore certifications and training from reputable organizations like the SANS Institute for security professionals.
- False Positives: Automated security tools can sometimes generate a high number of false positives, which can lead to “alert fatigue” and a loss of trust in the tools. Fine-tuning these tools is a continuous process.
- Metrics and Measurement: It can be difficult to measure the return on investment (ROI) of a DevSecOps program. Establishing clear metrics (e.g., Mean Time to Remediate, number of vulnerabilities found early) is essential for demonstrating value and securing continued investment.
The Future of Secure Software Delivery
The future of DevSecOps Maturity (Shift Left Security) is centered on intelligence, automation, and a holistic approach. We will see greater use of AI and machine learning to predict vulnerabilities, automate threat modeling, and provide more accurate security feedback. “Security as Code” will become the norm, where security policies are defined and managed alongside application code.
Ultimately, the goal is to make security a seamless, invisible, and natural part of the development process. As organizations move further along the maturity curve, they will realize that DevSecOps is not just a methodology but a fundamental enabler of business agility, allowing them to deliver innovative software at speed without compromising the trust and safety of their users.
Eager to learn more about the latest trends in cybersecurity, software development, and digital innovation? Explore our expert analysis and insights at jurnalin!